In a global landscape increasingly characterised by the pervasiveness of digital technology, which is an essential driver for the growth and continuity of any company's business, Poste Italiane aims to deploy state-of-the-art cybersecurity systems to effectively defend the company information assets from attacks and data theft.
This includes the Corporate Affairs - Information Security structure, which carries out a monthly cyber risk assessment for the Group. The methodology currently in use considers this risk from a purely technological point of view based on preventive technical security audits carried out on the three applications:
In order to ensure business continuity for the management of crises following sector-wide incidents, company-related incidents or extensive catastrophes affecting the Group, Poste Italiane has defined and implemented a business continuity plan based on an appropriate identification of the most critical systems, the potential threats to them and the countermeasures to be adopted. This plan must, therefore, describe the criteria, procedures, technical and organisational measures and instruments adopted for emergency management (Contingency Plan) and for the recovery of the operating conditions prior to a damaging event (Disaster Recovery) in compliance with the Service Level Agreements (SLAs) agreed with internal customers. To ensure its effectiveness over time, the Business Continuity Plan is tested and updated annually, and in any case in response to significant organizational, technological and infrastructural innovations or, more generally, in all situations capable of generate new risks, therefore, also on an infra-annually (e.g., quarterly, semi-annually).
During 2023, the implementation of the new BCM (Business Continuity Management) model continued, which, after the consolidation of financial services, was extended to the perimeter of payment services with the definition of the related Business Continuity Plan. Organisational and technological solutions for continuity were tested and training events on business continuity were held.
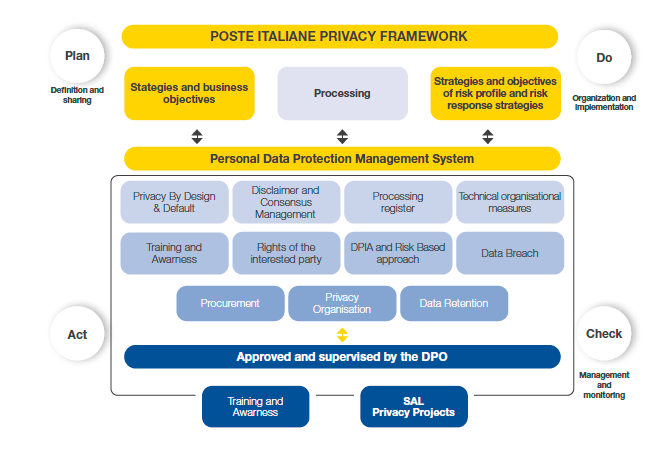
In this context, Poste Italiane has drawn up a Corporate Policy on Personal Data Protection and Privacy Guidelines and a Personal Data Protection Management System. The latter was introduced with the aim of ensuring uniform data management across the Group. The Guideline defines the corporate privacy model and implements the principles of Privacy by Design and Privacy by Default, underlining the Company's obligation to ensure adequate protection of personal data right from the design of products/services and IT systems, as well as ensuring compliance with privacy legislation in the predefined data collection and processing processes. Poste Italiane is also committed to ensuring proper management of data protection risks, by carrying out the periodic management review process at the Group level.
Poste Italiane's Privacy Framework was created with the aim of ensuring compliance with these obligations and aspiring to the continuous improvement of the management system. This framework provides an overview of the areas of intervention in which the relevant organisational and technical frameworks that have been developed operate, in order to provide continuous monitoring of the progress achieved.
Poste Italiane identifies for the entire Group the figure of the Data Protection Officer, a privacy expert who assumes responsibility for supervising compliance with the regulations on the protection of personal data by the data controller, as provided for by the GDPR, and who also ensures the drive towards continuous improvement.
The size and complexity of Poste Italiane's organisation means that a specific and targeted cybersecurity strategy needs to be outlined. For this reason, the Company set up the Computer Emergency Response Team (CERT) in 2013, which is made up of computer security experts who take care, 24 hours a day, every day of the year, of the protection of the company data through prevention, analysis and protection against cyber threats. CERT, whose services are certified to ISO/IEC 27001, ISO 9001 and ISO 37001, has implemented processes for the continuous monitoring and improvement of its services. Through internal audits, third-party audits, management reviews, KPI management, and regular reports to management, it ensures effective management and continuous improvement of its services and actions taken against defined lessons learned.
CERT has structured its services in such a way as to ensure the overall protection of Poste Italiane’s business, acting on a number of levels:
Poste Italiane maintains a solid collaborative relationship with the Postal and Communications Police. This collaboration includes activities aimed at preventing and combating offences related to the products and production processes of the services offered by the Poste Italiane Group. In addition, surveillance activities are carried out at Post Offices during scheduled payment periods. A task force was also set up with the task of analysing new cyber fraud methodologies, accompanied by the development of new cybersecurity tools. These measures were necessary in response to the changing scenarios and new types of malicious events. This has prompted the Company to quickly readjust its operations over the years, especially with reference to payment systems for e-commerce and financial and insurance services. In these areas, it was necessary to intensify control activities and upgrade the physical and IT security structures.
This includes the Corporate Affairs - Information Security structure, which carries out a monthly cyber risk assessment for the Group. The methodology currently in use considers this risk from a purely technological point of view based on preventive technical security audits carried out on the three applications:
- Vulnerability Assessment is the process of identifying, measuring and prioritising the vulnerabilities of a system. It is performed with special tools twice a year for each application;
- Code Review (Static and Dynamic) represents the process of checking the source code of an application to verify that the correct security controls are in place and that they are working as intended. By means of special tools, the verification is carried out of both the source code (“Static CR”) and of the code in execution (“Dynamic CR”);
- Penetration Test is the process of evaluating the security of a system or a network through the simulation of attacks (including hackers) that aim to gain undue access to the system. Being a time-consuming activity, it is performed on a specific perimeter of applications.
In order to ensure business continuity for the management of crises following sector-wide incidents, company-related incidents or extensive catastrophes affecting the Group, Poste Italiane has defined and implemented a business continuity plan based on an appropriate identification of the most critical systems, the potential threats to them and the countermeasures to be adopted. This plan must, therefore, describe the criteria, procedures, technical and organisational measures and instruments adopted for emergency management (Contingency Plan) and for the recovery of the operating conditions prior to a damaging event (Disaster Recovery) in compliance with the Service Level Agreements (SLAs) agreed with internal customers. To ensure its effectiveness over time, the Business Continuity Plan is tested and updated annually, and in any case in response to significant organizational, technological and infrastructural innovations or, more generally, in all situations capable of generate new risks, therefore, also on an infra-annually (e.g., quarterly, semi-annually).
During 2023, the implementation of the new BCM (Business Continuity Management) model continued, which, after the consolidation of financial services, was extended to the perimeter of payment services with the definition of the related Business Continuity Plan. Organisational and technological solutions for continuity were tested and training events on business continuity were held.
Personal Data Protection
Over the years, the Group has attributed great importance to the issue of personal data protection, constantly strengthening its corporate regulatory system and to ensure full compliance with current provisions and what is regulated within the General Data Protection Regulation (GDPR). Poste Italiane manages the control of the management review process at Group level, as set out in Article 32. The regulatory system, made up of procedures, guidelines and policies, is applied in relationships with all partners and suppliers to ensure correct management of risks related to the topic of privacy in all of the Group's operations. Failure to comply with the standards defined by the system, which may lead to violations, may result in the application of disciplinary sanctions to employees, in accordance with the provisions of the Poste Italiane CCNL (National Collective Labor Agreement). These sanctions are gradually harsher according to the seriousness of the breach (written warning, fine, suspension from work with deprivation of pay, dismissal without notice, etc.).In this context, Poste Italiane has drawn up a Corporate Policy on Personal Data Protection and Privacy Guidelines and a Personal Data Protection Management System. The latter was introduced with the aim of ensuring uniform data management across the Group. The Guideline defines the corporate privacy model and implements the principles of Privacy by Design and Privacy by Default, underlining the Company's obligation to ensure adequate protection of personal data right from the design of products/services and IT systems, as well as ensuring compliance with privacy legislation in the predefined data collection and processing processes. Poste Italiane is also committed to ensuring proper management of data protection risks, by carrying out the periodic management review process at the Group level.
Poste Italiane's Privacy Framework was created with the aim of ensuring compliance with these obligations and aspiring to the continuous improvement of the management system. This framework provides an overview of the areas of intervention in which the relevant organisational and technical frameworks that have been developed operate, in order to provide continuous monitoring of the progress achieved.
Poste Italiane identifies for the entire Group the figure of the Data Protection Officer, a privacy expert who assumes responsibility for supervising compliance with the regulations on the protection of personal data by the data controller, as provided for by the GDPR, and who also ensures the drive towards continuous improvement.

The Computer Emergency Response Team (CERT) and business continuity
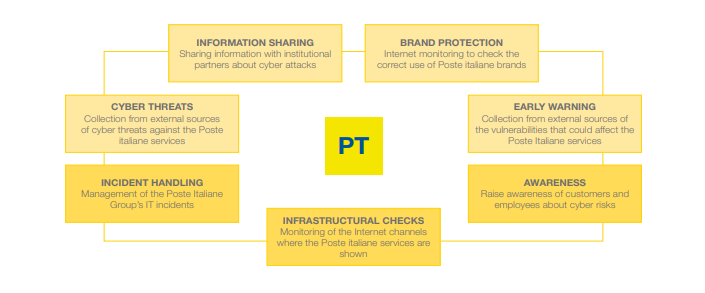
The size and complexity of Poste Italiane's organisation means that a specific and targeted cybersecurity strategy needs to be outlined. For this reason, the Company set up the Computer Emergency Response Team (CERT) in 2013, which is made up of computer security experts who take care, 24 hours a day, every day of the year, of the protection of the company data through prevention, analysis and protection against cyber threats. CERT, whose services are certified to ISO/IEC 27001, ISO 9001 and ISO 37001, has implemented processes for the continuous monitoring and improvement of its services. Through internal audits, third-party audits, management reviews, KPI management, and regular reports to management, it ensures effective management and continuous improvement of its services and actions taken against defined lessons learned.CERT has structured its services in such a way as to ensure the overall protection of Poste Italiane’s business, acting on a number of levels:
- External perimeter, which prevents attacks by collecting and exchanging information on threats and vulnerabilities that may affect the Group’s services;
- Internal perimeter, which protects the corporate infrastructure and responds to potential IT events.

| Information Sharing | Sharing information with institutional partners on cyber attacks. |
| Cyber Threat | Collection of malware against Poste Italiane from external sources. |
| Incident Handling | Management of IT incidents of the Poste Italiane Group. |
| Infrastructure Checks | Monitoring of the internet channels where Poste Italiane services are exposed. |
| Awareness | Raising customer and employee awareness of cyber attacks. |
| Early Warning | Collection of the vulnerabilities that may affect Poste Italiane services from external sources. |
| Brand Protection | Internet monitoring to verify the correct use of Poste Italiane brands. |
Poste Italiane maintains a solid collaborative relationship with the Postal and Communications Police. This collaboration includes activities aimed at preventing and combating offences related to the products and production processes of the services offered by the Poste Italiane Group. In addition, surveillance activities are carried out at Post Offices during scheduled payment periods. A task force was also set up with the task of analysing new cyber fraud methodologies, accompanied by the development of new cybersecurity tools. These measures were necessary in response to the changing scenarios and new types of malicious events. This has prompted the Company to quickly readjust its operations over the years, especially with reference to payment systems for e-commerce and financial and insurance services. In these areas, it was necessary to intensify control activities and upgrade the physical and IT security structures.


